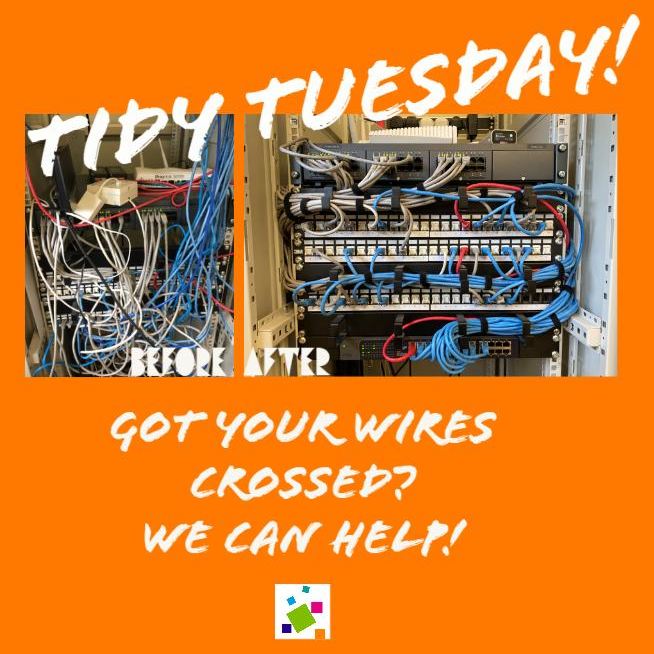
Got your wires crossed? Let us help!
Check out the epic work of our Helpdesk Heroes! We certainly worked our magic to make this “spaghetti junction” […]
How can we help?
01903 786287The latest news and information from inside Fentons and around the industry

Check out the epic work of our Helpdesk Heroes! We certainly worked our magic to make this “spaghetti junction” […]

🌟We are super proud to announce our recently qualified GOLD PARTNER status with one of Europe’s leading antivirus solution – […]

Sussex based IT company Fentons have successfully completed their annual Cyber Essentials renewal for 23-24. As part of our commitment […]

The essential 8 are cyber security controls that make it harder for criminals to access computer systems. We encourage your […]

Here are some top tips for working more securely from home. Beware of incoming scams One of the main risks […]

Outsourcing your IT to a managed IT service provider will save your business time and money. If you’re not already […]

Last year, Microsoft donated over $1.4 billion in software and services to nonprofit organisations. Their aim is to help nonprofits […]

Microsoft recently started rolling out the latest Windows 10 update. The update is named ‘Windows 10 May 2019 Update’ or […]

To quote Microsoft, “All good things must come to an end, even Windows 7”. From Jan 14, 2020, Microsoft will no […]

To help facilitate future growth, we are delighted to be working from a bright new office space in BizSpace – […]
We offer a free, no obligation consultation
The helpdesk is open tomorrow, 8:00am - 5:30pm*
*excludes bank holidays
Call us on 01903 786287